
Imperva SecureSphere - Database Firewall
Real-Time Protection Against Data Loss and Theft
Overview:
SecureSphere Database Firewall effectively protects databases from attacks, data loss and theft. With real-time monitoring, alerting and blocking, pre-built security policies and audit rules SecureSphere protects the most valuable database resources and ensures data integrity.
Database attacks such as SQL injection are on the rise and databases containing sensitive data are a top target for hackers and malicious insiders. Many databases are vulnerable and attackers take advantage of the fact that patching databases takes on average6-9 months. And recent incidents show that insiders may represent a significant risk to data security. By validating access requests and identifying material variance when users perform unexpected queries SecureSphere accurately blocks exploit attempts.
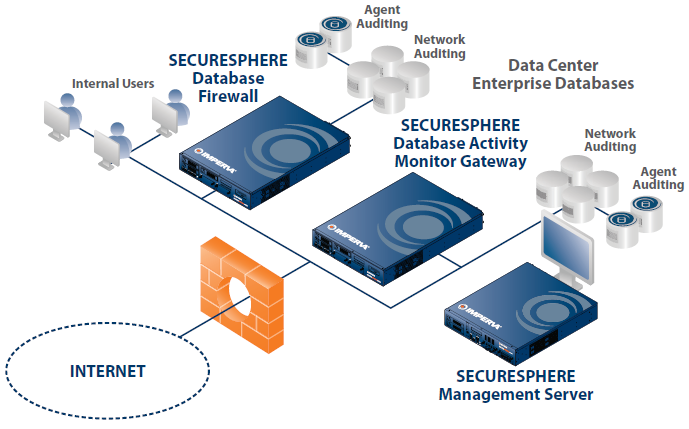
Unique to the industry, SecureSphere enables customers to optimize their DBF implementations by combining agent-based monitoring and network activity monitoring. SecureSphere database agents can be configured for monitoring local privileged activity exclusively, or for monitoring all database activity. SecureSphere can block attacks and unauthorized access both on the network and on the DB server. SecureSphere's hybrid architecture provides comprehensive database security with minimal overhead and unparalleled scalability.

Key Capabilities:
- Alert or block database attacks and abnormal access requests, in real time to protect against database attacks including SQL injection, Buffer overflow, Denial of Service and more
- Detect and virtually patch database software vulnerabilities reducing the window of exposure and impact of ad-hoc application fixes
- Audit all access to sensitive data by privileged and application users, and enforce corporate policies on data usage
- Accelerate incident response and forensic investigation through centralized management and advanced analytics
- Discover new databases and database objects in scope for security and compliance projects and automatically apply appropriate protection and audit policies
Features:
Real-Time Blocking of SQL Injection, DoS, and More
While selectively auditing access to sensitive data, SecureSphere monitors database activity in real-time and analyzes the traffic to the database looking for attacks at the protocol and OS level, as well as unauthorized SQL activity. Whether the attack source is an application or a privileged user, identified attacks can be blocked by preventing access to the database. SecureSphere can also monitor the database response and block data leakage. For added protection against sophisticated application attacks SecureSphere offers an integrated Web Application Firewall (WAF).
Preventing Unauthorized Access and Fraudulent Activity
SecureSphere identifies normal user access patterns to data using patented Dynamic Profiling technology. It establishes a baseline of all user activity including: DML, DDL, DCL, read-only activity (SELECTs) and usage of stored procedures. SecureSphere identifies material variances when users perform unexpected queries or violate access policies and alerts or blocks the access. Users performing unauthorized requests to the database can also be quarantined until their access rights have been reviewed and approved.
Virtual Patching Prevents Vulnerability Exploits
SecureSphere mitigates identified database vulnerabilities by enabling a security policy (i.e. Virtual Patch) to block exploit attempts. Surveys have shown that most organizations are behind on database patch deployment due to the need to validate a vendor patch before production rollout. However, while databases are un-patched, they're exposed to attackers looking to capitalize on the vulnerability. Virtual Patching can be deployed immediately to minimize the window of exposure and reduce the risk of a data breach.
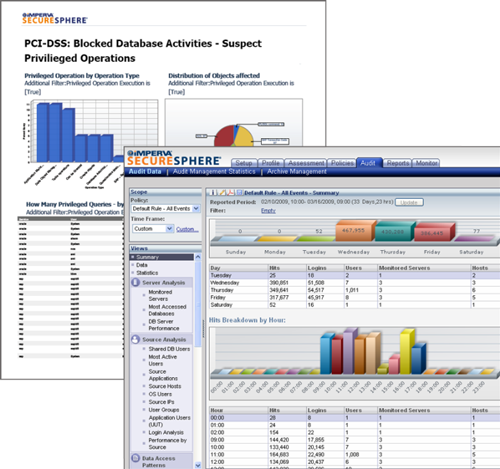
Continuous Auditing, Analytics for Forensic Investigations
SecureSphere continuously monitors and audits all database operations, in real-time. The detailed audit trail provide organizations with the complete 'Who, What, When, Where, and How' of each transaction. The detailed audit trail enables security teams to perform forensic investigations on data breach events. Interactive audit analytics simplifies identification of trends and patterns that indicate security risks or compliance problems.
Policy Enforcement, Streamlined Compliance Reporting
SecureSphere includes a complete set of predefined customizable security and audit policies. The policies can be quickly implemented to enforce separation of duties through global or granular access controls on any database environment. Reports on security events can be scheduled to run automatically and are available in PDF or HTML formats. Specific reports are designed for demonstrating compliance with SOX, PCI DSS, HIPAA and other data privacy laws. Security alerts can be sent to SIEM, ticketing systems and other 3rd party solutions in order to streamline business processes.
Effective User Rights Management Across Databases
SecureSphere streamlines the review and management of user rights across heterogeneous databases. With User Rights Management, organizations can establish an automated process for access rights review, identify excessive user rights and demonstrate compliance with regulations such as SOX, PCI 7, and PCI 8.5.
Classifying Data in Scope for Compliance and Security
SecureSphere detects all database systems in scope for security and compliance projects through automated discovery and classification of sensitive data. Identifying databases and objects that contain sensitive and regulated data helps organizations fundamentally understand which databases and objects should be audited and support implementation of granular audit policies. In addition, discovery and classification provides details needed for prioritizing vulnerability remediation efforts.
Deployment and Coverage
Optimized architecture, flexible deployment options:
SecureSphere offers multiple deployment options, with non-intrusive network monitoring appliances, lightweight SecureSphere agents, 3rd party audit log collection, or a hybrid mix. SecureSphere drop-in physical and virtual appliances provide high performance monitoring and auditing capabilities that can scale to support any environment – from SMBs to large Enterprises. SecureSphere agents eliminate 'blind-spots' by auditing activity that can't be seen on the network. SecureSphere's flexible architecture simplifies the design of custom deployments that fit unique topology and business needs.
Deployment:
Unparalleled Database Security and Compliance
SecureSphere addresses all aspects of database security and compliance with industry-best database auditing and real-time protection that will not impact performance or availability. With its multi-tier architecture, SecureSphere scales to support the largest database installations. By automating security and compliance, it is not surprising that thousands of organizations choose Imperva SecureSphere to safeguard their most valuable assets.
- Non-inline Network Monitoring: Activity monitoring with zero impact on database performance or availability
- Transparent Inline Protection: Drop-in deployment and industry-best performance
- Agent-based Monitoring and Blocking: Lightweight software agents that monitor and block direct privileged activities and network traffic
- Gateway Clustering: Cost-effective resilient database auditing
- Supported Database Platforms: Oracle, Oracle Exadata, Microsoft SQL Server, IBM DB2 (on Linux, UNIX, Windows, z/OS and DB2/400), IBM IMS on z/OS, IBM Informix, IBM Netezza, SAP Sybase, Teradata, Oracle MySQL, PostgreSQL, and Progress OpenEdge
Features and Appliance Specifications:
| Specification | Description |
|---|---|
| Supported Database Platforms |
|
| Deployment Modes |
|
| Performance Overhead |
|
| Centralized Management |
|
| Centralized Administration |
|
| Database Audit Details |
|
| Privileged Activities |
|
| Access to Sensitive Data |
|
| Security Exceptions |
|
| Data Modification |
|
| Stored Procedures |
|
| Triggers |
|
| Tamper-Proof Audit Trail |
|
| Fraud Identification |
|
| Data Leak Identification |
|
| Database Security |
|
| Platform Security |
|
| Network Security |
|
| Policy Updates |
|
| Real-Time Event Management and Report distribution |
|
| Server Discovery |
|
| Data Discovery and Classification |
|
| User Rights Management (add-on option) |
|
| Vulnerability Assessment |
|
Documentation:
Download the Imperva SecureSphere Database Security Products Datasheet (PDF).
Download the Imperva SecureSphere Appliances Datasheet (PDF).
