
Imperva SecureSphere - Data Security Suite
Full Visibility and Control for Applications and Databases
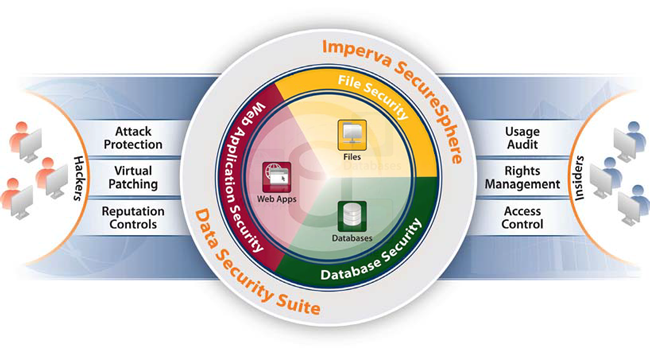
Overview:
SecureSphere Data Security Suite is the market leading data security and compliance solution. SecureSphere protects sensitive data from hackers and malicious insiders, provides a fast and cost-effective route to regulatory compliance and establishes a repeatable process for data risk management.
Powering the SecureSphere Data Security Suite is a common platform that provides flexible deployment options, unified management, deep analytics and customizable reporting. The SecureSphere platform enables enterprise scalability and accelerates time to value.
Underscoring Imperva's commitment to data security excellence, the Imperva Application Defense Center (ADC) is a world-class security research organization that maintains SecureSphere's cutting edge protection against evolving threats.
Key Capabilities:
- Protects Web applications from complex, large scale online attacks
- Secures and audits access to business-critical databases and files
- Focuses forensic analysis for effective incident response
- Reduces data by detecting sensitive data, mitigating vulnerabilities and removing excessive rights
SecureSphere Data Security Product Lines

Database Security
SecureSphere Database Security solutions secure sensitive data stored in databases. SecureSphere provides full visibility into data usage, vulnerabilities and access rights and enables security, audit and risk professionals to improve data security and meet regulatory compliance mandates.

File Security
SecureSphere File Security solutions protect sensitive files on file servers, storage devices, content repositories, and meet regulatory compliance mandates such as PCI DSS 11.5. SecureSphere provides full visibility into data ownership, usage and access rights and enables executives, auditors, security and IT managers to improve file data security and meet regulatory compliance mandates.

Web Application Security
SecureSphere Web Application Security solutions protect web applications from cyber attacks. SecureSphere continuously adapts to evolving threats and enables security professionals, network managers and application developers to mitigate the risk of a data breach and address regulatory compliance requirements such as PCI DSS 6.6.

SecureSphere for SharePoint
Microsoft SharePoint provides easy access to business-critical data through intranet, extranet, and public-facing applications. So when that information is sensitive or regulated, security is a major concern. SecureSphere for SharePoint is designed specifically for this platform to give you the highest level of visibility and access control for your SharePoint system data. As a result, you can ensure application and data security, and even cut costs by accelerating time-to-compliance.
SecureSphere Platform
The SecureSphere platform is the cornerstone of Imperva's award-winning data security products. It includes centralized management and reporting framework, physical and virtual appliance delivery options, and server agent software that extends data security to host systems. With its flexible deployment options and administration capabilities, SecureSphere provides organizations the scalability, adaptability, and management needed to deploy state of the art data security solutions.
Features:
- Fully Integrated Data Security Suite – The Data Security Suite is the complete integrated package of the other SecureSphere product lines- Web Application Firewall, Discovery and Assessment Server, Database Activity Monitoring, and Database Firewall.
- Accurate Protection against Web application and Database Attacks – SecureSphere detects multiple types of security violations, including unexpected application or database requests, known (signature-based)attacks, privilege abuse, protocol violations, and session exploits.
- Complete Visibility – From the database to the application end user, the SecureSphere Data Security Suite can monitor and track the full transaction. SecureSphere audits all types of activities, including all types of SQL operations and local, privileged access by DBAs. Supporting heterogeneous database deployments, SecureSphere is the clear choice for data auditing, monitoring and forensics.
- User Accountability – The SecureSphere Data Security Suite makes individual users accountable even when user connections are pooled by an application server. Imperva’s innovative Universal User Tracking capability offers four different user tracking mechanisms to correctly identify end users regardless of how the users authenticate and access the database.
- Discovery and Assessment – SecureSphere offers server and sensitive data discovery, configuration assessment, and behavior assessment. SecureSphere enables organizations to identify and prioritize risks, mitigate vulnerabilities, and document compliance.
- Data Leak Prevention – SecureSphere detects and can optionally block sensitive data leaks, such as credit card and social security numbers, from Web applications and databases.
- Automated, Intuitive Management – Imperva’s unique Dynamic Profiling technology automatically learns the structure, elements, and expected usage of protected applications and databases.
- Enterprise-grade Centralized Management – Scaling to protect large, distributed data centers, the MX Management Server centralizes the configuration, monitoring and reporting of multiple appliances.
- Integrated Risk Management – Includes innovative Risk Dashboard to visualize and prioritize data security activities based on risk.
- Business Relevant Reporting – SecureSphere includes a powerful reporting framework with both pre-defined and fully-customizable reports that offers instant visibility for security and compliance requirements.
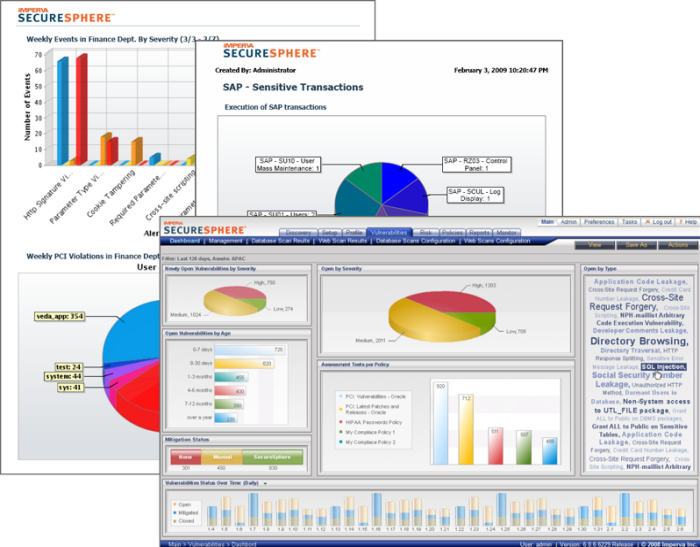
Addressing the Full Data Security and Compliance Life Cycle
With an increasing number of industry and government regulations, businesses must implement a repeatable process that addresses data governance and data protection. The SecureSphere Data Security Suite empowers organizations to establish a successful framework for security and standards compliance.
Because many regulations are vague and subject to interpretation, organizations have wasted valuable time and expense coordinating separate compliance initiatives. However, even though the number of regulatory mandates is escalating, more and more regulations present common themes.
Imperva has outlined an actionable set of steps that helps organizations meet many of the regulatory requirements that oversee data governance and data protection.
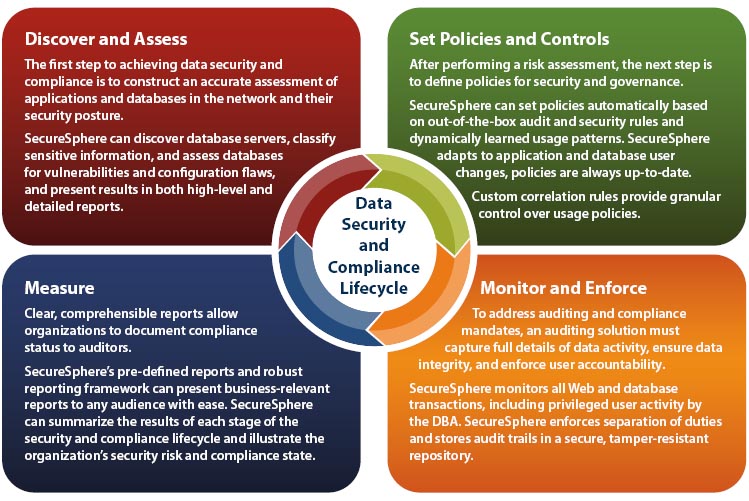
This iterative compliance framework comprises the following four steps:
- Discover and Assess
- Set Policies and Controls
- Monitor and Enforce
- Measure
Using this framework, organizations can satisfy compliance requirements, as well as align business objectives, implement controls, and ensure robust security.
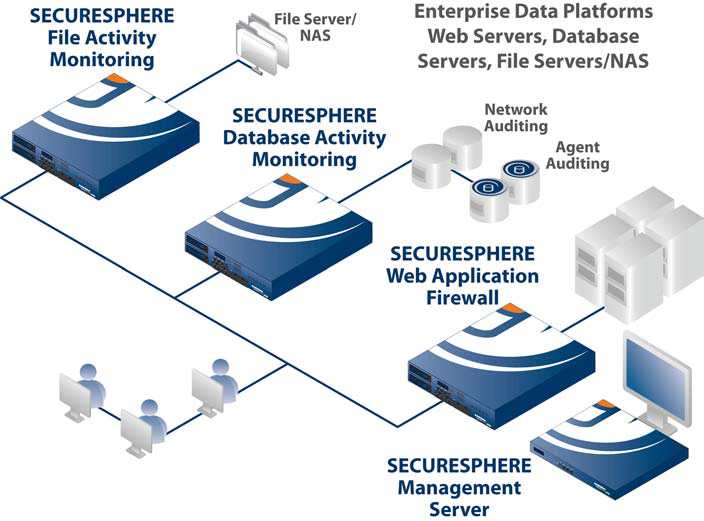
Deployment:
The Industry Standard in Data Security, Auditing, and Compliance
The SecureSphere® Data Security Suite unifies audit, security, and risk management for business databases and the applications that use them. In a single, comprehensive security platform, the market-leading Web Application Firewall, Database Activity Monitoring, and Database Firewall prevent sensitive data theft, protect against data breaches, secure applications, and ensure data confidentiality.
Combining visibility and control for both applications and databases, SecureSphere delivers full activity monitoring from the database to the accountable application user and is widely recognized for its overall ease of management and deployment.
Features and Appliance Specifications:
| Specification | Description |
|---|---|
| Integrated Suite |
|
| Databases Supported |
|
| Data Discovery and Classification |
|
| Vulnerability Assessment |
|
| Database Audit |
|
| Database Security |
|
| Web Securiy |
|
| HTTPS/SSL Inspection |
|
| Web Services Security |
|
| Platform Security |
|
| Network Security |
|
| Advanced Protection |
|
| Fraud Prevention |
|
| Data Leak Prevention |
|
| Policy/Signature Updates |
|
| Management |
|
| Administration |
|
| Monitoring |
|
| High Availability |
|
| Deployment Modes |
|
Documentation:
Download the Imperva SecureSphere Data Security Suite Datasheet (PDF).
Download the Imperva SecureSphere Database Security Products Datasheet (PDF).
Download the Imperva SecureSphere File Security Products (PDF).
Download the Imperva SecureSphere Web Application Security Products (PDF).
