
Imperva SecureSphere - Web Application Firewall
Protect Critical Web Applications and Data
Overview:
Your website receives a continuous barrage of attacks. If hackers uncover a crack in your defenses, they can steal your application data, defraud your users, and take down your website.
The SecureSphere Web Application Firewall stops web attacks and prevents costly data breaches and downtime. Combining multiple defenses, SecureSphere accurately pinpoints and blocks attacks without blocking your customers. It offers drop-in deployment and automated management. Certified by ICSA Labs, SecureSphere satisfies PCI 6.6 compliance and provides ironclad protection against the OWASP Top Ten.
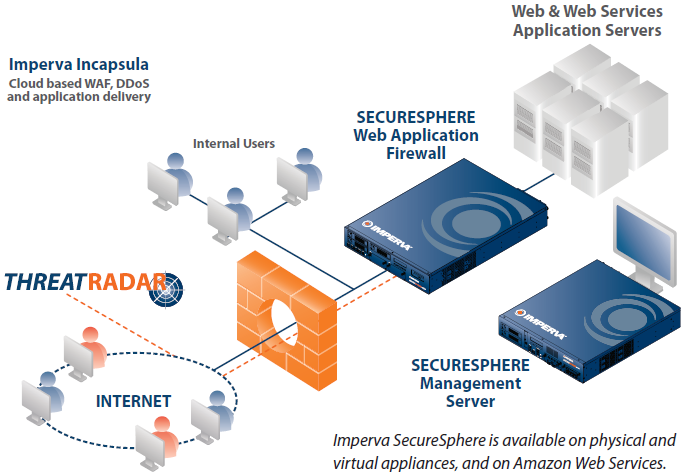
Imperva SecureSphere
The market-leading SecureSphere Web Application Firewall has transformed the way businesses protect their applications by automating web security and providing flexible, transparent deployment. With its comprehensive protection and low administrative overhead, SecureSphere is the ideal solution to secure valuable web assets and achieve PCI compliance. Imperva SecureSphere is available on physical and virtual appliances, and on Amazon Web Services.

Key Capabilities :
- Automatically learns protected applications and user behavior
- Updates Web defenses with research-driven intelligence on current threats
- Accurately blocks attempts to exploit known and unknown vulnerabilities
- Identifies traffic originating from known malicious sources with ThreatRadar
- Correlates request attributes across security layers and over time to detect sophisticated, multi-stage attacks
- Virtually patches vulnerabilities by integrating with Web application vulnerability scanners, reducing the window of exposure and impact of emergency fixes
- Fully addresses PCI 6.6
- Offers high performance and transparent, drop-in deployment
Firewall Features:
Automated Learning of Applications and User Behavior
A Web application firewall must understand application structure, elements and expected user behavior in order to accurately detect attacks. Imperva's patented Dynamic Profiling technology automates this process by profiling all application elements and building a baseline or "white list" of acceptable user behavior. It also automatically incorporates valid application changes into the application profile over time. Dynamic Profiling eliminates the need to manually configure—and update—application URLs, parameters, cookies, and methods.
Research-Driven Security Policies
Powered by the Imperva Application Defense Center (ADC), an international security research organization, SecureSphere offers the most complete set of application signatures and policies available. The ADC investigates vulnerabilities reported by Bugtraq, CVE®, Snort®, and underground forums and performs primary research to deliver the most up-to-date and comprehensive Web attack protection available.
Adaptable Protection from Large Scale, Automated Attacks
An add-on service to the SecureSphere Web Application Firewall, ThreatRadar Reputation Services offers powerful protection against automated attacks and botnets. ThreatRadar aggregates near real-time feeds of known attack sources, bots, phishing URLs, and anonymizing services to block malicious traffic before an attack can be attempted. Up-to-date geolocation data enables businesses to restrict access by geographic location.
ThreatRadar Community Defense provides crowd-sourced threat intelligence to stop emerging threats by collecting attack data from SecureSphere Web Application Firewalls.
DDoS Protection Service
SecureSphere Web Application Firewall stops application-layer DDoS attacks, but massive network-based DDoS attacks can still saturate your Internet connection and prevent traffic from ever reaching your site. The best place to combat network DDoS threats is in the cloud – before the attack can clog your network. DDoS Protection Service for SecureSphere is a secure, ultra-high capacity service that safeguards organizations from crippling DDoS attacks. DDoS Protection Service for SecureSphere can be deployed quickly and can scale on demand to mitigate multi-gigabit DDoS attacks.
Virtual Patching Through Vulnerability Scanner Integration
For immediate patching of application vulnerabilities, SecureSphere can import assessment results from WhiteHat, IBM, Cenzic, NT OBJECTives, Qualys, and others and create custom policies to block known vulnerabilities. Virtual patching reduces the window of exposure and the cost of emergency fix and test cycles.
Protection Against Malware-based Fraud
ThreatRadar Fraud Prevention, an add-on service to the SecureSphere Web Application Firewall, enables organizations to rapidly provision and manage fraud security without updating web applications. By integrating with leading fraud security vendors, SecureSphere can transparently identify and stop fraudulent transactions. It also provides powerful monitoring and enforcement capabilities, allowing businesses to centrally manage WAF and fraud policies together.
HTTP Protocol, Platform, and XML Protection
SecureSphere enforces HTTP standards compliance to prevent protocol exploits and evasion techniques. Fine-grained policies allow administrators to enforce strict adherence to RFC standards or allow minor deviations. With over 8,000 signatures, SecureSphere safeguards the entire application infrastructure including applications and web server software. Flexible, automated XML security policies protect web services, SOAP, and Web 2.0 applications.
Granular Correlation Policies Reduce False Positives
SecureSphere distinguishes attacks from unusual, but legitimate, behavior, by correlating Web requests across security layers and over time. SecureSphere's Correlated Attack Validation capability examines multiple attributes such as HTTP protocol conformance, profile violations, signatures, special characters, and user reputation, to accurately alert on or block attacks with the lowest rate of false positives in the industry.
Customizable Reports for Compliance and Forensics
SecureSphere's rich graphical reporting capabilities enable customers to easily understand security status and meet regulatory compliance. SecureSphere provides both pre-defined and fully-customizable reports. Reports can be viewed on demand or emailed on a daily, weekly, or monthly basis.
Monitoring for In-Depth Analysis of Attacks
Alerts can be easily searched, sorted, and directly linked to corresponding security rules. SecureSphere's monitoring and reporting framework provides instant visibility into security, compliance, and content delivery concerns. A real-time dashboard provides a high-level view of system status and security events.
Imperva Incapsula
Imperva Incapsula is an easy and affordable service that integrates a PCI-certified Web Application Firewall, DDoS protection, load balancing and failover on top of a global content delivery network. Imperva Incapsula requires no hardware or software installations, and no web application changes, only a simple DNS change, so even business units or other organizations without dedicated security or IT staff can rest assured that their web applications and data are safe.
Deployment:
Multiple SecureSphere Deployment Options
- Transparent Layer 2 Bridge: Drop-in deployment and industry-best performance
- Reverse Proxy and Transparent Proxy: Provide content modification, such as cookie signing and URL rewriting
- Non-inline Monitor: Zero risk monitoring and forensics
- High Availability: IMPVHA, VRRP, fail open interfaces, existing redundancy options, non-inline deployment
Specifications:
| Specification | Description |
|---|---|
| Web Securiy |
|
| Application Attacks Prevented |
|
| HTTPS/SSL Inspection |
|
| Web Services Security |
|
| Web Fraud Prevention |
|
| Content Modification |
|
| Platform Security |
|
| Network Security |
|
| Advanced Protection |
|
| Data Leak Prevention |
|
| Policy/Signature Updates |
|
| Authentication |
|
| User Awareness |
|
| Deployment Modes |
|
| Management |
|
| Administration |
|
| Logging/Monitoring |
|
| High Availability |
|
| Solution Delivery Option |
|
| Web Application Vulnerability Scanner Integration |
|
| Enterprise Application Support |
|
| TCP/IP Support |
|
| Certification(s) |
|
View Demo:
Why have a Web Application Firewall?
Documentation:
Download the Imperva SecureSphere Web Application Security Products Datasheet (PDF).
Download the Imperva SecureSphere Web Application Firewall Datasheet (PDF).
